🎯 Objective
In this report we show how we perform a Wi-Fi network scan to check:
- Which devices (antennas, mobiles, PCs) are connected.
- Which services and ports are active.
- That firewall filtering and security are working properly.
🔍 What is a network scan?
A network scan is a process that allows us to discover and analyze devices connected to a given IP range. For this task, we use two complementary tools:
1) Host discovery (ARP Sweep) 🖧
- Tool:
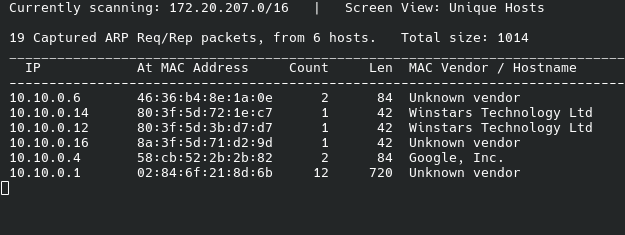
netdiscover - Function: detects live IPs in the LAN by resolving their MAC addresses.
- Results in our Wi-Fi:
- ✅ Antennas:
10.10.0.12,10.10.0.14,10.10.0.16. - ✅ Gateway/IPFire:
10.10.0.1. - ✅ Guest client:
10.10.0.4(Pixel 3a XL). - ✅ Other temporary devices (
10.10.0.6,10.10.0.8).
- ✅ Antennas:
📌 Command used:
netdiscover -r 10.10.0.0/24
2) Port and service scanning 🔓
- Tool:
nmap(with Zenmap GUI). - Function: performs a SYN Scan to discover open ports, active services, and OS fingerprints.
- Expected results in our network:
- Web ports 80/443 active on gateway and antennas.
- DNS (53/tcp/udp) active on gateway.
- Auxiliary services like 3128 (proxy/captive helper).
📌 Command used:
nmap -T4 -A -v 10.10.0.0/24
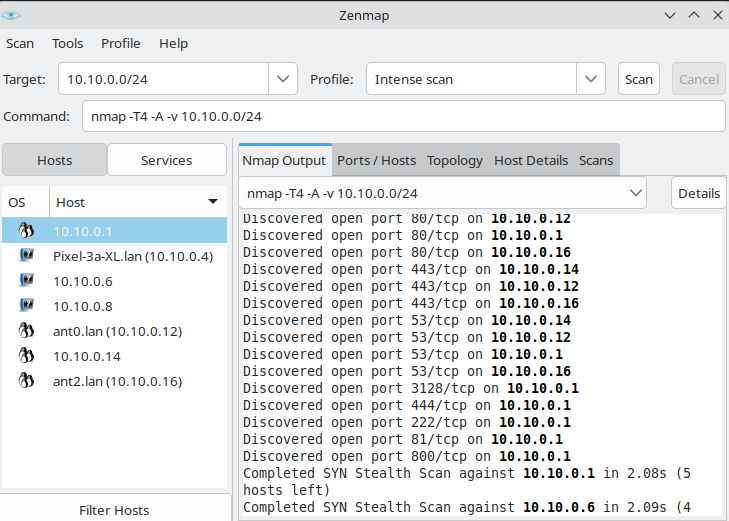
✅ Conclusion: Everything works as expected → gateway responds properly, antennas are accessible, and no unusual services are open on client devices.
🧱 Security and captive portal
The network is secured with a deny-by-default model:
- 🌐 HTTP (80) traffic redirected to the welcome portal.
- 🔒 HTTPS (443) allowed only to authorized domains.
- 📡 Antennas always whitelisted.
- 🔄 VPN tun1 as the main outgoing path.
- 🛑 DNS traffic blocked unless it passes through the official resolver.
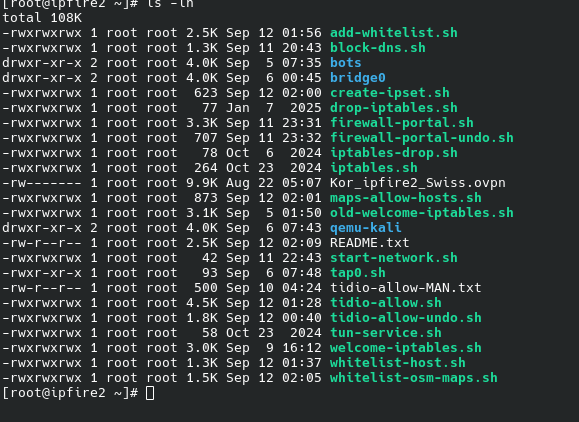
🗂️ Scripts in /root ready to deploy ⚡
We created these scripts to cover different needs. Quick description:
add-whitelist.sh→ Adds a domain/IP to the whitelist.block-dns.sh→ Blocks unauthorized DNS resolutions.bridge0/→ Bridge network configuration.create-ipset.sh→ Creates ipset lists for filtering.drop-iptables.sh→ Drops all traffic (full lockdown).firewall-portal.sh→ Activates the main captive portal.firewall-portal-undo.sh→ Reverts portal rules.iptables.sh→ Base iptables configuration.Kor_ipfire2_Swiss.ovpn→ OpenVPN profile to Switzerland.maps-allow-hosts.sh→ Whitelist for OpenStreetMap tiles.qemu-kali/→ Config for Kali Linux VM.start-network.sh→ Brings up tun1 and applies firewall rules.tap0.sh→ Creates a TAP interface.tidio-allow.sh→ Allows Tidio chat connections.tidio-allow-undo.sh→ Removes Tidio from whitelist.tun-service.sh→ Controls OpenVPN service (start/stop).welcome-iptables.sh→ Redirects HTTP to welcome page.whitelist-host.sh→ Quickly whitelists an IP.whitelist-osm-maps.sh→ Specific whitelist for OSM map servers.
✅ Current status
- 📡 Antennas active and working correctly.
- 🔑 Gateway responding with expected open ports.
- 📱 Guest client detected and controlled.
- ⚙️ Scripts ready for immediate adjustments.
🚀 Conclusion
With this system of monitoring and automation, the Wi-Fi network at Korman Vilares Resort remains secure, controlled, and efficient, ensuring reliable connectivity for users and stability for internal services.
